Malicious attackers are leveraging browser notifications as a vector for phishing attacks to distribute malicious links using a new command-and-control (C2) platform called Matrix Push C2.
“This browser-native fileless framework leverages push notifications, fake alerts, and link redirects to targeted victims across operating systems,” Blackfog researcher Brenda Robb said in a report Thursday.
In these attacks, potential targets are tricked into allowing browser notifications through social engineering on malicious or legitimate websites.
Once a user agrees to receive notifications from a site, the attacker leverages the web browser’s built-in web push notification mechanism to send alerts that appear to be sent by the operating system or the browser itself. This leverages a trusted brand, a familiar logo, and compelling language to keep the game going.
These include alerts about things like suspicious logins and browser updates, as well as helpful “confirm” and “refresh” buttons that, when clicked, redirect you to a fake site.
What makes this a smart technique is that the entire process takes place through the browser without the need to first infect the victim’s system through other means. In some ways, this attack is similar to ClickFix in that users are tricked into following specific instructions to compromise their systems, thereby effectively bypassing traditional security controls.
That’s not all. This attack is also a cross-platform threat as it is carried out via a web browser. This essentially joins the browser applications on the platform that subscribe to malicious notifications into a pool of clients, giving the adversary a persistent communication channel.
Matrix Push C2 is offered as a Malware-as-a-Service (MaaS) kit to other threat actors. It is sold directly through crimeware channels (usually via Telegram or cybercrime forums) on a tiered subscription model. Prices are approximately $150 for one month, $405 for three months, $765 for six months, and $1,500 for one year.
“Payments are accepted in cryptocurrencies and buyers communicate directly with operators for access,” BlackFog founder and CEO Dr. Darren Williams told Hacker News. “Matrix Push was first observed in early October and has been active ever since. There is no evidence of older versions, previous brands, or long-standing infrastructure. All indicate this is a newly launched kit.”
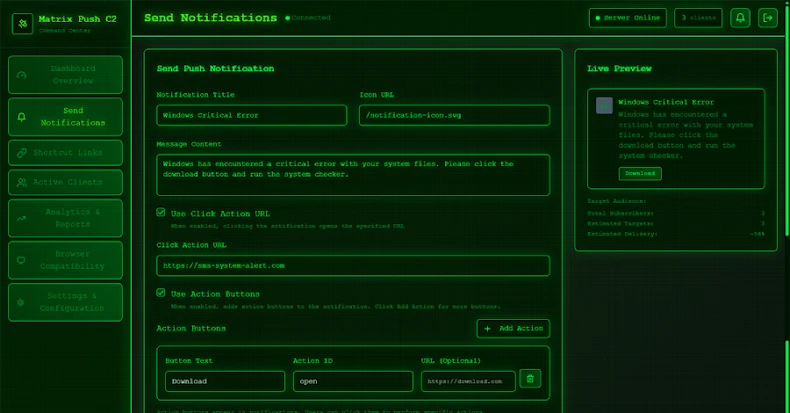
Accessible as a web-based dashboard, the tool allows users to send notifications, track each victim in real-time, determine which notifications a victim interacted with, create shortened links using the built-in URL shortener, and even log installed browser extensions, including cryptocurrency wallets.
“The core of the attack is social engineering, and Matrix Push C2 includes configurable templates to maximize the authenticity of fake messages,” Robb explained. “An attacker can easily theme a phishing notification or landing page to impersonate a well-known company or service.”
Some of the supported notification validation templates are associated with well-known brands such as MetaMask, Netflix, Cloudflare, PayPal, and TikTok. The platform also includes an “Analytics and Reports” section that allows customers to measure the effectiveness of their campaigns and make adjustments as needed.
“Matrix Push C2 represents a change in the way attackers seek to gain initial access and exploit users,” BlackFog said. “Once a user’s endpoint (computer or mobile device) is affected by this type of impact, an attacker may escalate the attack over time.”
“They may deliver additional phishing messages to steal credentials, trick users into installing more persistent malware, or even leverage browser exploits to gain deeper control over the system.The end goal is often to steal data or monetize access by exfiltrating cryptocurrency wallets or exfiltrating personal information.”
Attacks exploiting Velociraptors are on the rise
The development comes after Huntress said it had observed a “significant increase” in attacks armed with the legitimate Velociraptor digital forensics and incident response (DFIR) tool over the past three months.
On November 12, 2025, the cybersecurity vendor announced that attackers deployed Velociraptor after gaining initial access by exploiting a flaw in Windows Server Update Services (CVE-2025-59287, CVSS score: 9.8) that was patched by Microsoft late last month.
The attackers then allegedly conducted reconnaissance and launched discovery queries aimed at gathering details about users, running services, and configurations. The attack was contained before it could progress further, Huntress added.
This discovery shows that attackers are not only using custom C2 frameworks, but also leveraging off-the-shelf offensive cybersecurity and incident response tools.
“We have seen threat actors use legitimate tools for a long time, so we know that Velociraptor is not the first dual-use open source tool to emerge in attacks, and it will not be the last,” Huntress researchers said.