Cybersecurity researchers have discovered vulnerable code in a legacy Python package that could pave the way for a supply chain compromise of the Python Package Index (PyPI) through domain takeover attacks.
Software supply chain security company ReversingLabs announced that it has discovered a “vulnerability” in a bootstrap file provided by a build and deployment automation tool named zc.buildout.
“The script automates the process of downloading, building, and installing the necessary libraries and tools,” said security researcher Vladimir Pezo. “Specifically, when the bootstrap script runs, it fetches and runs the installation script for packages distributed from python-distribute(.)org, a legacy domain currently sold at a premium price point while being managed to drive advertising revenue.”
PyPI packages that contain bootstrap scripts to access the domain in question include tornado, pypiserver, slapos.core, roman, xlutils, and testfixtures.
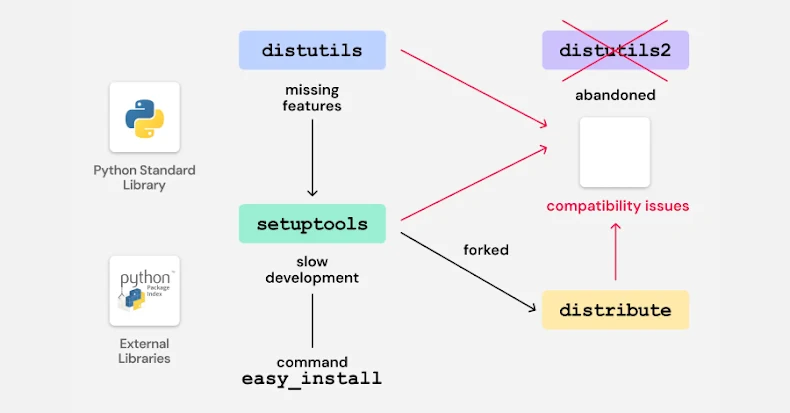
The core of the issue involves an old bootstrap script (‘bootstrap.py’) that was used with the zc.buildout tool to initialize the Buildout environment. The Python script also supported the ability to install a packaging utility called “Distribute”, a short-lived fork of the Setuptools project, into the local environment.
To accomplish this, the Distribute installation script (‘distribute_setup.py’) is pulled from python-distribute(.)org, a domain that has been up for sale since 2014. The idea in adding the option was to tell the bootstrap script to download and install the Distribute package instead of the old Setuptools package to manage buildout eggs and dependencies.
It’s important to note that the Distribute fork was born in the absence of active development of Setuptools, the primary package management tool in use at the time. However, Distribute’s functionality was merged into Setuptools in 2013, and Distribute was deprecated.
The issue identified by ReversingLabs is related to the fact that many packages continue to ship bootstrap scripts that attempt to install Distribute by default or when command line options (‘-d’ or ‘–distribute’) are specified. This, combined with the fact that the domain in question is open to theft, exposes users to potential risk as an attacker could weaponize this setting to provide malicious code and steal sensitive data when the bootstrap script is executed incorrectly.
Although some of the affected packages have taken steps to remove their bootstrap scripts, the slapos.core package continues to ship vulnerable code. It is also included in development and maintenance versions of Tornado.
Another important aspect to consider here is that the bootstrap script is not automatically run during package installation and is written in Python 2. This means that the script cannot be run in Python 3 without modification. However, the mere presence of this file leaves an “unnecessary attack surface” that an attacker can exploit if a developer is tricked into executing code that triggers the execution of the bootstrap script.
The threat of domain takeover is not theoretical. In 2023, it was revealed that the npm package fsevents was compromised by a malicious attacker who took control of unclaimed cloud resources hosted at fsevents-binaries.s3-us-west-2.amazonaws(.)com and pushed a malicious executable to users who had certain versions of the package installed (CVE-2023-45311, CVSS score: 9.8).
“The problem lies in the programming pattern of retrieving and executing a payload from a hard-coded domain, which is a common pattern in malware that exhibits downloader behavior,” Pezo said. “By not formally deprecating the Distribute module, vulnerable bootstrap scripts remained and an unknown number of projects were left exposed to potential attacks.”
This disclosure comes after HelixGuard discovered a malicious package named “spellcheckers” on PyPI. Although the package claims to be a spelling error checking tool using OpenAI Vision, it contains malicious code designed to connect to an external server, download the next stage payload, and execute a remote access trojan (RAT).
This package was first uploaded to PyPI by user named leo636722 on November 15, 2025, and has been downloaded 955 times. Download is no longer possible.
“This RAT can receive remote commands and execute attacker-controlled Python code via exec(), allowing complete remote control of the victim host,” HelixGuard said. “Once a user installs and runs a malicious package, a backdoor is activated, allowing the attacker to remotely control the user’s computer.”