Kubernetes’ Ingress Nginx Controllers disclose a set of sets to Kubernetes’ Ingress Nginx Controllers, which can immediately put more than 6,500 clusters at risk by exposing components to the public Internet.
The vulnerabilities (CVE-2025-24513, CVE-2025-24514, CVE-2025-1097, CVE-2025-1098, and CVE-2025-1974) have assigned a CVSS score of 9.8 and employing ingressmare by cloud security company Wiz. It is worth noting that the drawbacks do not affect the Nginx Ingress controller. This is another Ingress controller implementation for Nginx and Nginx Plus.
“The exploitation of these vulnerabilities could lead to unauthorized access to all secrets stored in all namespaces of the Kubernetes cluster by attackers, leading to cluster takeover,” the company said in a report shared with Hacker News.
Ingressnightmare affects the entry controller component of Kubernetes’ Ingress nginx controllers at its core. Approximately 43% of cloud environments are vulnerable to these vulnerabilities.
The Ingress Nginx controller uses Nginx as a reverse proxy and load balancer, allowing HTTP and HTTPS routes to services within it from outside the cluster.
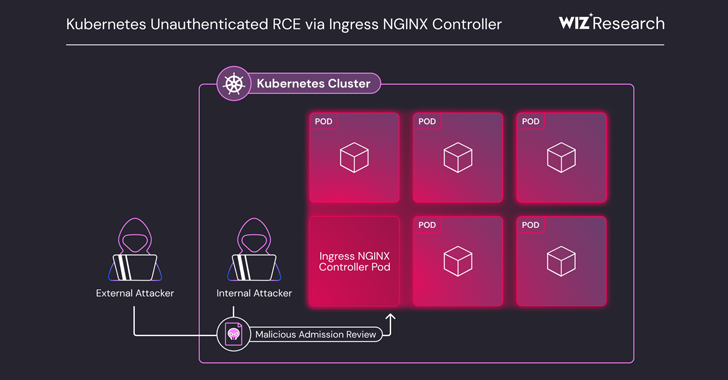
The vulnerability exploits the fact that admission controllers deployed within the Kubernetes pods are accessible over the network without authentication.
Specifically, code is executed in the Ingress Nginx controller pod, including remotely injecting any Nginx configuration by sending a malicious Ingress object (aka AdzentReview Request) directly to the entrance controller.
“The increased privileges of admission controllers and unlimited network accessibility create important escalation paths,” Wiz explained. “By exploiting this flaw, attackers can run arbitrary code and access all cluster secrets across the namespace, which could lead to a complete cluster takeover.”
The drawbacks are listed below –
- CVE-2025-24513 (CVSS score: 4.8) – Inappropriate input validation vulnerability that could lead to directory traversal within a container.
- CVE-2025-24514 (CVSS score: 8.8) – config can be injected into Nginx using the Auth-URL Ingress annotation.
- CVE-2025-1097 (CVSS score: 8.8) – config can be injected into NGINX using the Auth-TLS-Match-CN Ingress annotation.
- CVE-2025-1098 (CVSS score: 8.8) – Any configuration can be injected into Nginx using mirror target and mirror host ingress annotations.
- CVE-2025-1974 (CVSS score: 9.8) – A well-known attacker who has no access to the POD network can achieve arbitrary code execution in the context of an Ingress Ninx Controller under certain conditions

In an experimental attack scenario, threat actors can use NGINX’s client body buffer feature to upload malicious payloads to the pod in the form of shared libraries, then send an AdmissimentReview request to the admission controller.
This request then contains one of the above-mentioned configuration directive injections that cause the shared library to be loaded, effectively leading to the execution of remote code.
Hillai Ben-Sasson, a cloud security researcher at Wiz, told Hacker News that the attack chain involves injecting an inherently malicious configuration, which is used to read sensitive files and execute arbitrary code. This allows attackers to exploit powerful service accounts to read Kubernetes secrets and ultimately drive cluster acquisitions.
Following responsible disclosure, the vulnerabilities are addressed in nginx controller versions 1.12.1, 1.11.5, and 1.10.7.
Users are advised to update to the latest version as soon as possible and to ensure that the Anizent Webhook endpoint is not exposed externally.
As a mitigation, we recommend restricting only the Kubernetes API server to access the enrollment controller, and temporarily disable the enrollment controller component if not needed.