A now-patched critical security flaw affecting Google Cloud Platform (GCP) Composer could have been exploited to enable remote code execution on cloud servers through a supply chain attack technique known as dependency confusion.
The vulnerability is codenamed Cloud Importer According to Tenable Research.
“This vulnerability could have allowed an attacker to hijack an internal software dependency that Google pre-installs into each Google Cloud Composer pipeline orchestration tool,” security researcher Liv Matan said in a report shared with The Hacker News.
First documented by security researcher Alex Birsan in February 2021, dependency confusion (also known as a substitution attack) refers to a type of software supply chain compromise in which a package manager is tricked into pulling a malicious package from a public repository instead of the intended file of the same name in an internal repository.
This allows threat actors to launch large-scale supply chain attacks by publishing counterfeit packages to public package repositories with the same name but higher version number as a package developed in-house by a company.
As a result, package managers unknowingly download malicious packages from public repositories instead of private ones, and replace existing package dependencies with the unauthorized packages.
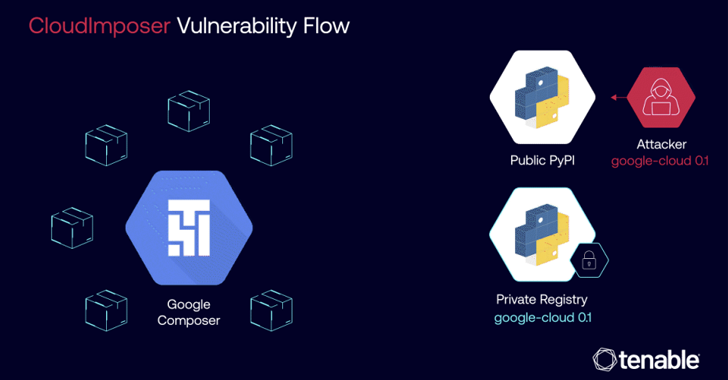
The issue identified by Tenable is similar in that a malicious package could be uploaded to a Python Package Index (PyPI) repository under the name “google-cloud-datacatalog-lineage-producer-client” and pre-installed on all Composer instances with elevated privileges.
Although Cloud Composer expects the packages in question to be version pinned (i.e. version 0.1.0), Tenable has discovered that using the `–extra-index-url` argument during the `pip install` command can result in dependency confusion, as it prioritizes retrieving the package from a public registry.
With these permissions, an attacker could execute code, steal service account credentials, and move laterally to other GCP services within the victim’s environment.
Following responsible disclosure on January 18, 2024, Google fixed the issue in May 2024 by ensuring that packages could only be installed from private repositories, and also added the extra precaution of verifying package checksums to ensure package integrity and validate that they have not been tampered with.
The Python Packaging Authority (PyPA) has been aware of the risks posed by the “–extra-index-url” argument since at least March 2018, and is said to be urging users not to use PyPI if they need to pull internal packages.
“Packages are expected to be unique down to their name and version, so two wheels with the same package name and version are treated as indistinguishable by pip,” PyPA members noted at the time. “This is an intentional feature of package metadata and is unlikely to change.”
As part of the fix, Google is recommending that developers use the “–index-url” argument instead of the “–extra-index-url” argument, and that GCP customers use Artifact Registry virtual repositories if they require multiple repositories.
“The ‘–index-url’ argument mitigates the risk of dependency confusion attacks by only searching for packages in the registries defined as the value provided to that argument,” Matan said.