According to Huntress, the security flaws recently revealed on Gladinet Centrestack have also affected Trifox’s remote access and collaboration solutions, which have compromised seven different organizations to date.
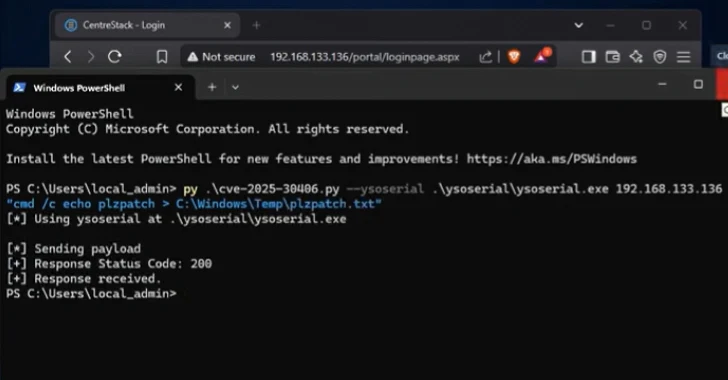
I tracked the AS CVE-2025-30406 (CVSS score: 9.0), a vulnerability refers to the use of hard-coded encryption keys that allow Internet-accessible servers to be exposed to remote code execution attacks.
This is addressed in Centrestack version 16.4.10315.56368, released on April 3, 2025. The vulnerability is said to have been misused as a zero day in March 2025, but the exact nature of the attack is unknown.
Currently, according to Huntress, the weaknesses have also affected Gladinet Triofox up to version 16.4.10317.56372.
“By default, previous versions of Triofox software have the same hard-coded encryption key in their configuration files, allowing them to easily abuse remote code execution,” says John Hammond, Huntress’ chief cybersecurity researcher, in a report.

Telemetry data collected from the partner base revealed that Centrestack software was installed on approximately 120 endpoints, with seven unique organizations being affected by vulnerability exploitation.
The oldest signs of compromise date back to 11 April 2025 at 16:59:44 UTC. It has been observed that attackers are exploiting flaws to download and sideload DLLs using encoded PowerShell scripts. This is an approach seen in a recent attack using a flaw in CrushFTP, then performs lateral movement and installs MeshCentral for remote access.
https://www.youtube.com/watch?v=-zpjygzdujm
Huntress also said that the attacker has been identified as running in-packet PowerShell commands to install Meshagent by running various enumeration commands. That said, the exact scale and ultimate goal of the campaign is currently unknown.
In light of aggressive exploitation, it is essential for Gladinet Centrestack and Triofox users to update their instances to the latest version to prevent potential risks.